Blog
Bridging the Gap Between Privileged Access Management & Identity Management
by DGITUser | Mar 20, 2024 | Articles
Bridging the Gap Between Privileged Access Management & Identity Management In today's rapidly evolving cybersecurity landscape, organisations...
The CIPC hack and what it means for South African companies
by DGITUser | Mar 20, 2024 | Articles
The CIPC hack and what it means for South African companies Recently, the Companies and Intellectual Property Commission (CIPC) of South Africa fell...
Fortifying Kenya’s Digital Frontier: Navigating the Evolving East African Cybersecurity Landscape
by DGITUser | Mar 20, 2024 | Articles
Fortifying Kenya's Digital Frontier: Navigating the Evolving East African Cybersecurity Landscape The rise of digitalization and digital economies...
Nigeria’s Cyber Security Battleground: Inside the Rise of Ransomware and AI-Powered Scams
by DGITUser | Mar 20, 2024 | Articles
Nigeria's Cyber Security Battleground: Inside the Rise of Ransomware and AI-Powered Scams As the digital landscape evolves, so to do the threats...
Navigating the Evolving Cybersecurity Landscape with AI
by DGITUser | Feb 1, 2024 | Articles
In the ever-evolving world of cybersecurity, a new era of threats has emerged, one that is more personal, targeted, and sophisticated than ever...
AI Governance: Navigating the New Frontier of Technology
by DGITUser | Jan 25, 2024 | Articles
In the ever-evolving landscape of technology, 2023 has been marked by the dazzling rise of AI, crowned as the buzzword of the year. The...
Securing Digital Resilience: The Essential Role of Contingency DDoS Protection in Business Continuity
by DGITUser | Jan 18, 2024 | Articles
In the ever-evolving landscape of cybersecurity, Distributed Denial of Service (DDoS) attacks remain a formidable threat to organizations worldwide....
Ransomware on the rise: How to safeguard your organisation
by DGITUser | Jan 11, 2024 | Articles
In a digital age shadowed by cyber threats, an alarming 71% of organizations have been victims of ransomware attacks, each costing an average of...
Navigating the Cybersecurity Horizon: Check Point’s Projections for 2024
by DGITUser | Dec 17, 2023 | Articles
As we venture deeper into the digital landscape, Check Point Research (CPR) unveils its comprehensive projections for 2024, revealing a surge in...
Decoding Firewall Security Standards: A Comprehensive Guide to Network Protection
by DGITUser | Dec 13, 2023 | Articles
Maintaining a robust network security posture is paramount in the digital age, and at the heart of this defence lies firewall security standards....
Safeguarding Your Inbox: The Power of AI-Driven Email Security
by DGITUser | Dec 7, 2023 | Articles
In an era where email is the lifeblood of business communication, the threat landscape has evolved, with phishing campaigns leveraging generative AI...
The Biggest Threats to Online Retailers This Holiday Season
by DGITUser | Dec 1, 2023 | Uncategorized
As the holiday season unfolds with joyous festivities and shoppers immerse themselves in the spirit of giving, a shadow looms over the digital...
WAF vs. Firewall – Decoding the Web Application & Network Firewalls Dilemma
by DGITUser | Nov 29, 2023 | Articles
In the realm of cybersecurity, the distinction between a Web Application Firewall (WAF) and a traditional network firewall is a pivotal...
How XDR Differs from Other Security Technologies
by DGITUser | Nov 24, 2023 | Articles
In the ever-evolving landscape of cybersecurity, the sheer number of acronyms and security solutions can be overwhelming. Today, we're diving into...
Taming the Alert Tsunami: Overcoming Alert Deafness in Cybersecurity
by DGITUser | Nov 7, 2023 | Articles
In today's fast-paced world of software development and cybersecurity, the constant barrage of notifications and alerts has become a major issue for...
How Darktrace’s AI Technology Enhances Email Security Through Employee Engagement
by DGITUser | May 18, 2023 | Articles
Email security has always been a significant concern for IT teams, but the traditional approach of either excluding employees entirely or including...
Top 5 Best Practices for Implementing Zero Trust Security
by DGITUser | May 15, 2023 | Articles
In the world of cybersecurity, Zero Trust Security is widely viewed as one of the most effective approaches to security because it removes the...
How to Strengthen Your Cloud Security with Check Point’s Cloud Guard
by DGITUser | May 8, 2023 | Articles, Cloud Security
As more businesses move their operations to the cloud, the threat of cyberattacks increases exponentially. Protecting your assets in the cloud is...
The Advantages of AI-Powered Email Solutions for Security Teams
by DGITUser | May 4, 2023 | Articles
Security teams are often burdened with a variety of tasks, such as dealing with an increased attack surface, enabling remote work, and managing...
Implementing PAM to Achieve Zero Trust Security Principles
by DGITUser | Apr 26, 2023 | Articles
The concept of zero trust security has been around for over a decade, with Forrester Research Inc. coining the term back in 2010. Originally, zero...
Secure Your Organisation’s Unmanaged Devices with Check Point Harmony Browse
by DGITUser | Apr 12, 2023 | Articles
In today's digital landscape, securing an organisation's devices is crucial for maintaining data confidentiality and protecting against cyber...
Discover High-Impact Attack Paths with Darktrace
by DGITUser | Apr 6, 2023 | Articles
In the world of cybersecurity, it's essential to understand the potential pathways that attackers might use to compromise an organisation's...
Maximising Efficiency & Security: 6 Top Strategies for Cybersecurity Teams
by DGITUser | Apr 4, 2023 | Articles
In the fast-paced world of cybersecurity, time is money, and it's essential to find ways to optimise efficiency while ensuring digital safety....
The Fundamentals of a Zero-Trust Cybersecurity Model according to Imperva
by DGITUser | Apr 1, 2023 | Articles
In the United States, government has recommended the zero-trust cybersecurity model as a way to ensure baseline security practices and mitigate...
Tips to Maximise the Effectiveness of MFA Implementation
by DGITUser | Mar 30, 2023 | Articles
In today's digital world, authentication is the new entry point into our networks, and it's critical to ensure maximum security. With the rise of...
Leveraging AI for Effective Cyber Risk Management
by DGITUser | Mar 25, 2023 | Articles, Cloud Security, Data Security
As organisations continue to face cyber threats and vulnerabilities, the need for effective cyber risk management practices has become increasingly...
The Best Practice for Mitigating Cloud Identity Security Risks
by DGITUser | Mar 18, 2023 | Articles, Cloud Security
Cloud computing is by no means a new concept; it has been around since the 1950s when technologies such as mainframe computing, utility computing,...
A glimpse into the future of data security in 2023
by DGITUser | Feb 28, 2023 | Articles
Let's talk about the future of data security. As we move further into 2023, Imperva predicts that we'll see some major changes in the way companies...
How Imperva Cloud WAF Protects Your Web Applications from Cyber Threats
by DGITUser | Feb 17, 2023 | Application Security, Articles
In today's digital age, web applications have become a critical component for many medium and large organisations. These organisations rely on their...
Continued Misconfigurations in Cloud-Managed Infrastructure Pose a Major Risk to Data Security
by DGITUser | Jan 31, 2023 | Articles
In recent years, cloud-hosted data has become increasingly popular, with spending on cloud services reaching $178 billion in 2021, a 37% increase...
The key to effective Attack Surface Management
by DGITUser | Jan 23, 2023 | Articles
Effective Attack Surface Management (ASM) is essential for understanding and mitigating cyber risks to your organisation. It can be broken down into...
Protect Your Assets in the Cloud with Check Point’s Comprehensive Security Solution
by DGITUser | Jan 16, 2023 | Articles
As businesses continue to shift their operations to the cloud, it's essential to have a comprehensive security solution in place to protect your...
The problem with passwords
by DGITUser | Dec 31, 2022 | Articles
This year, as cyber incidents continued to be one the rise, one of the key topics of consideration was the role of strong authentication in...
Curbing Shadow IT in your organisation
by DGITUser | Mar 17, 2022 | Articles
“Shadow IT refers to (the use of) IT devices, software and services outside the ownership (approval) or control of IT organisations.” – Gartner The...
Understanding the mechanics of a data breach
by DGITUser | Mar 17, 2022 | Articles
Definition: A data breach is a cyber-attack in which sensitive or confidential data has been accessed or disclosed to an unauthorised individual or...
The key to effective SaaS Asset Management
by DGITUser | Mar 17, 2022 | Articles
Increasing levels of remote work and the accompanying migration to the cloud has seen a renewed emphasis on data protection, proactive threat...
Adopting proactive cybersecurity with Threat Hunting
by DGITUser | Mar 17, 2022 | Articles
With more than 2,200 cyberattacks per day, it’s easy for organisations to start feeling like sitting ducks. The alarming increase in cybersecurity...
How to better identify a social engineering scam
by DGITUser | Feb 19, 2022 | Articles
Social engineering, the practice of manipulating a victim into believing they are communicating with a trusted individual or platform, so they give...
Simple steps to reducing your cyberattack surface
by DGITUser | Feb 3, 2022 | Articles
As we mark two years of operating under the new normal of Work from Anywhere, Hybrid Work and increased Bring Your Own Device environments, it goes...
Is your organisation prepared for a supply chain attack?
by DGITUser | Jan 27, 2022 | Articles
If the numbers are anything to go by, now more than ever is a highly stressful time to be tasked with maintaining the cybersecurity posture of an...
2022 cybersecurity strategies for startups
by DGITUser | Jan 21, 2022 | Articles
Few things evolve as rapidly as the state of cybersecurity and what should be prioritised to protect an organisation from malicious actors. In...
Eliminating the man in the middle
by DGITUser | Jan 6, 2022 | Articles, Data Security
The time is 12:53pm. You just got to your favourite coffee place to seal the deal with an exciting prospective client. Suddenly you remember that...
Top Cybersecurity Trends To Lookout For in 2022
by DGITUser | Jan 4, 2022 | Application Security, Articles, Cloud Security, Data Security, Mobile Security, Network Security, User Security
The world of technology is an ever changing one with cybersecurity being the epitome of that. Cybersecurity is an area in which the inability to...
Only The Agile Will Survive
by DGITUser | Dec 20, 2021 | Articles
A lot has been said about the importance of a business being agile. Business agility is crucial as the ability to adapt to your environment in real...
4 Cybersecurity Lessons Learnt In 2021
by DGITUser | Dec 17, 2021 | Articles
What a year it’s been and there’s certainly a lot to learn as we complete year 2 of the dreaded “new normal”. March 2020 marked the start of a drive...
Eliminating The Fear of The Unknown with Zero-Trust
by DGITUser | Nov 28, 2021 | Articles
The future of technology is limitless. Technological advances have been accelerated through increased network agility, integrated artificial...
Authentication methods your organisation should consider
by DGITUser | Nov 21, 2021 | Articles
‘Password123’. Gone are the days where this was all you needed to secure your desktop or keep people out of your inbox. Now with an ever-increasing...
What is Identity and Access Management (IAM)?
by DGITUser | Nov 14, 2021 | Articles
Identity and Access Management in regards to cybersecurity refers to a framework of policies, processes, and technologies that enable organisations...
The Endpoint of the new normal
by DGITUser | Nov 9, 2021 | Articles
Over the last year and a half, what has been dubbed the “new normal” has slowly but surely become the “normal”. It is now common place for sensitive...
Bringing Self-Defence to Cybersecurity
by DGITUser | Nov 2, 2021 | Articles
The day-to-day challenges faced by the modern CISO are monumental. You are charged with keeping your organisation’s most valuable assets safe from...
Why sharing is caring in Cloud Security
by DGITUser | Oct 25, 2021 | Articles
Over the years software as a service (SaaS), platform as a service (PaaS) and infrastructure as a service (IaaS) have really taken off with many...
DataGroupIT opens new Lagos & Nairobi office
by DGITUser | Oct 18, 2021 | Articles
DataGroupIT is proud to announce we have opened two new offices across West and East Africa. Our new offices are in Lagos and Nairobi and offer our...
The new normal in cybersecurity is now just ‘normal’
by DGITUser | Oct 18, 2021 | Articles
Looking back on early 2020, one can be forgiven for believing that the call to stay home and work remotely was only going to last for a couple of...
A simple guide to adopting Zero-Trust
by DGITUser | Oct 11, 2021 | Articles
Implementing cybersecurity best practice in your organisation should always be viewed as a journey and not an event. The on-going process requires...
The next natural step in cloud-based architecture: SASE
by DGITUser | Sep 27, 2021 | Articles
Many of us are old enough to remember when cloud computing was considered to be a passing trend. In today’s world, technologies come and go faster...
How to build your cybersecurity team the effective way
by DGITUser | Sep 20, 2021 | Articles
The age old saying 'teamwork makes the dream work' is widely applicable in a multitude of environments and situations. Often applied to the sporting...
Tapping into the power of proactive cybersecurity with self-learning AI
by DGITUser | Sep 13, 2021 | Articles
As the world enhances its approach to dealing with a growing number of cybersecurity threats, the utilization of artificial intelligence to monitor...
How bad is it out there? The State of Cybersecurity in 2021
by DGITUser | Sep 8, 2021 | Articles
Has a week gone by without at least one headline that left you slightly nervous about the state of cybersecurity and whether your organisation could...
Top cybersecurity trends in the financial sector
by DGITUser | Aug 27, 2021 | Articles, Data Security
As digitalisation in the global financial services sector and digital banking channel adoption gather pace, the risks posed by cybercriminals will...
The AI solution to rising cybersecurity threats
by DGITUser | Aug 20, 2021 | Articles, User Security
According to the World Economic Forum Global Risks Report 2021, cybersecurity failure was rated alongside extreme weather, climate action failure...
The role of automation in cybersecurity
by DGITUser | Aug 12, 2021 | Articles
The old proverb, Fight fire with fire, is taking on new meaning in the battle CISOs and CIOs are waging against increasingly well-resourced and...
The value of managed security services in your organisation
by DGITUser | Aug 5, 2021 | Articles, Network Security
IT has become mission critical, and increasingly acts as business’s trusted advisor in an increasingly digital marketplace. Companies have been...
Cybersecurity and the impact of working from home
by DGITUser | Jul 22, 2021 | Articles, User Security
At the issuance of lockdown orders, working from home largely sounded like heaven for most employees and even companies as they saw the opportunity...
Exploring the future of cloud solutions with Distributed Cloud
by DGITUser | Jul 22, 2021 | Articles, Cloud Security
Since making a splash in the early part of the last decade, Cloud Computing has continued to evolve in order to cater to the varying use cases...
Understanding the cybersecurity mesh and its impact on your enterprise
by DGITUser | Jul 19, 2021 | Articles, Data Security, Network Security
In a rapidly evolving digital world, one can be forgiven for feeling overwhelmed with the width and breadth of threats, innovations, and...
The rise of ransomware in 2021
by DGITUser | Jul 14, 2021 | Articles
The level of espionage, stealth and tech jargon associated with cybercrime can easily lead one to believe that “it only happens in the movies”. That...
Rethinking cybersecurity attacks and how to manage them
by DGITUser | Jul 11, 2021 | Articles, Data Security
Attacks are going to happen. As sure as the sun rises in the East and sets in the West, you can trust that an attempt on your network at one point...
To VPN or Not to VPN?
by siteadmin | Oct 27, 2020 | Network Security, User Security
Over the past few years, VPN vulnerabilities have been in the spotlight and talked about everywhere. There is always some vulnerability being abused...
Imperva’s Mobile Security App
by siteadmin | Oct 27, 2020 | Mobile Security
How many apps do you currently have on your mobile device? Is this number a total across both your personal and professional devices? Did you know...
Multi-Vendor Firewall Change Tracker for Network Security Admins
by siteadmin | Oct 27, 2020 | Network Security
As the spread of COVID-19 is forcing employees to work remotely, it’s put an unprecedented strain on organizations’ network and security teams, a...
Zero Trust Architecture: Best Practices for Safer Networks
by siteadmin | Oct 27, 2020 | Data Security, Network Security, User Security
A zero trust architecture enables organizations to prioritize access and restrictions. The goal is to implement a zero trust policy across all...
Monitoring 802.1X EAP: What You Need to Know
by siteadmin | Oct 27, 2020 | Network Security
First Thing’s First As we’ve written about previously, the standard authentication protocol used on encrypted networks is Extensible Authentication...
Multi-factor authentication offers effective security, but not all solutions are created equal
by siteadmin | Oct 27, 2020 | Cloud Security, User Security
Reports published by Proofpoint recently documenting MFA vulnerabilities in Microsoft 365 (Office 365) have likely caused concern among Microsoft...
Increase SSO security by going passwordless
by siteadmin | Oct 27, 2020 | Cloud Security, User Security
The acceleration of digital transformation initiatives to support the remote workforce has, in turn, sped up the development of cloud-based...
5 Best Practices for Securing Privileged Access and Identities for the Cloud Management Console
by siteadmin | Oct 27, 2020 | Cloud Security, User Security
Over the next few weeks, we’ll explore best practices for securing privileged accounts and identities in common cloud scenarios. This series can...
AI email security: Understanding the human behind the keyboard
by siteadmin | Oct 27, 2020 | User Security
At the heart of any email attack is the goal of moving the recipient to engage: whether that’s clicking a link, filling in a form, or opening an...
Notice the unnoticed: Threat Hunting by SandBlast Agent
by siteadmin | Oct 27, 2020 | User Security
By Yaelle Harel and Boaz Barzel Threat Hunting is a proactive approach for finding and remediating undetected cyber-attacks. It is a process that...
Avoid Alert Fatigue: How to Automatically Get Rid of WAF False Positive
by siteadmin | Oct 27, 2020 | Application Security, Data Security
Alert fatigue – introducing false positives in WAF All WAF experts know what it’s like handling massive amounts of alerts. They’re also very likely...
How AI detected a hacker hiding in an energy grid within hours of deployment
by siteadmin | Oct 27, 2020 | Network Security
A cyber-criminal had already made the first steps of a critical intrusion at a European energy organization when the company deployed AI for cyber...
Cloud-sourcing: Using Global Threat Intelligence to Instantly Protect Your Cloud Assets
by siteadmin | Oct 26, 2020 | Cloud Security
By Jonathan Maresky, CloudGuard Product Marketing Manager, published October 21, 2020 When it comes to security in the cloud, companies face...
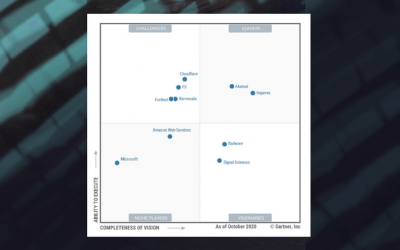
Imperva A Seven-Time Magic Quadrant Leader and Named Highest for Completeness of Vision for WAF
by siteadmin | Oct 26, 2020 | Application Security
Gartner has published its 2020 Gartner Magic Quadrant for Web Application Firewalls (WAF) and Imperva has been named a Leader for the seventh...
DataCenter Security Event
by siteadmin | Sep 18, 2020 | Events
Data centre security broadly refers to the array of technologies and practices used to protect a facility’s physical infrastructure and network...
Case Study
by siteadmin | Sep 2, 2020 | Case Studies
Coming soon