Implementing cybersecurity best practice in your organisation should always be viewed as a journey and not an event. The on-going process requires regular revision, adaptation, and evolution. One of the most recent steps in improving organisational security approach is the adoption of a Zero Trust approach.
However, questions still remain around what constitutes Zero Trust and what it means to deploy the approach in your enterprise. And so below we’ve compiled a selection of key touch points around Zero-Trust that aim to help organisations understand it better:
What Is Zero Trust?
As highlighted by Palo Alto Networks, ‘Zero Trust is a strategic approach to cybersecurity that secures an organisation by eliminating implicit trust and continuously validating every stage of a digital interaction.’
In essence the basic premise is that not a single digital asset, outside as well as within your security perimeter, should be trusted. This is particularly critical in an age where there are constant changes to IT environments through the increase of the hybrid work structure. As such, least privilege is no longer a consideration, it is a must. The process of authentication, authorisation and verification of data must be employed at all stages of digital interactions, to ensure the robustness of your security posture is upheld.
Why you should consider a Zero Trust Strategy
Risk mitigation should always be at the forefront of a cybersecurity strategy. With cyberattacks becoming increasingly inevitable, the priority is then to ensure they fail or at the bare minimum have little impact to operations.
Through Zero Trust as a strategic framework, your organisation can isolate cyber-events in the case of a compromise and ensure that there is a significantly reduced risk of malicious actors spreading throughout the system.
Eliminating implicit trust to users, applications and infrastructure also helps your organisation attain better security outcomes as the level of security checks is elevated.
Lastly, Zero Trust provides your organisation with a clear and simplified security posture that in turn can reduce the cost of IT resources through the removal of obsolete and redundant solutions.
How do you become a Zero Trust enterprise?
Palo Alto Networks has highlighted a best practice approach to adopting Zero Trust. It entails assessing what your current security surface looks like and what needs to be employed to reduce acute risk in order to achieve resilience.
A glimpse of their approach appears as follows:
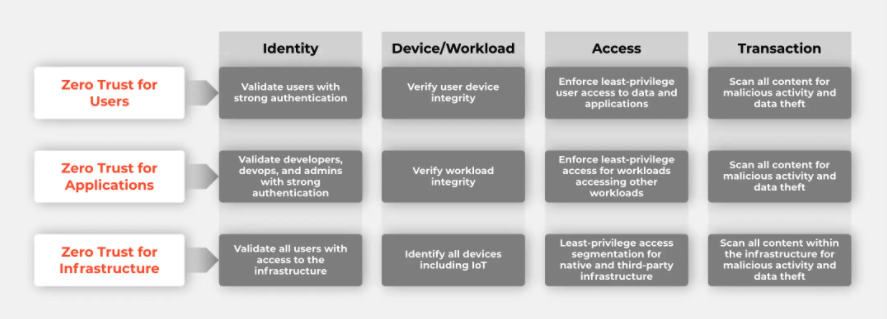
Where should you begin in your Zero Trust journey?
Adopting any new technology or approach can appear like a daunting task. And in a fair number of instances, it can present both technical and structural challenges to the enterprise. However, if the vision remains clear that protecting your data is paramount, the adoption of the solution becomes a non-negotiable and more palpable to the team.
The start of the Zero-Trust journey involves understanding that it should consider the full ecosystem of controls – network, endpoint, cloud, application, the Internet of Things, identity and more – which organisations rely on for protection.
Palo Alto Networks in particular has a comprehensive Zero Trust framework that covers all key touch-points of the cybersecurity infrastructure.
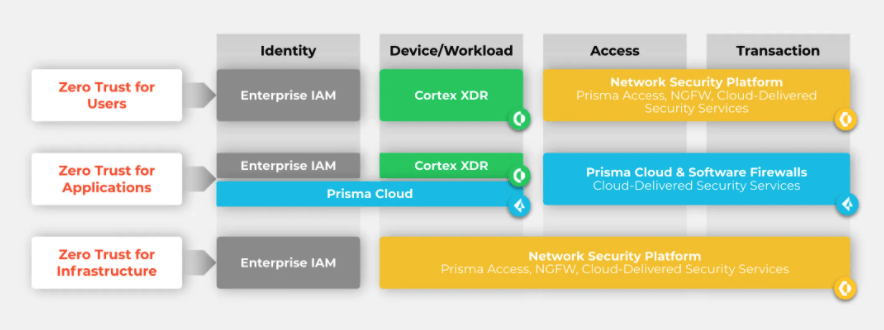
What’s next?
DataGroupIT has extensive history in deploying Zero-Trust solutions to clients across South, East and West Africa alongside our industry leading partner, Palo Alto. To find out more about how these solutions can empower your organisation, kindly contact us on info@datagroupit.com, we look forward to the opportunity to explore strategic solutions that are tailored to your needs.




