Has a week gone by without at least one headline that left you slightly nervous about the state of cybersecurity and whether your organisation could be the next big target?
One of the most common questions floating around the boardroom of late is, ‘How bad is it out there?’, often followed up by ‘Could we be next?’ The cold hard truth is it is bad, and there’s a strong probability that even if you aren’t next, you may be in one or another set of crosshairs.
So, what does this mean in practical terms? How does the conversation evolve from fear-mongering to tangible insights that can help guide your next steps?
The first step lies in understanding the landscape.
What’s Happening Out There?
It is well documented that cyberattacks continue to increase both locally and on a global scale. Reports have listed an eye-watering 97% year on year increase in cyber-attacks in the EMEA region alone.
While there are multiple types of attacks, the majority of them are in the form of ransomware, supply chain fraud and targeted phishing attacks. According to the Centre for Strategic & International Studies, in July 2021 alone there were 14 newsworthy attacks including the highly publicised ransomware attack on Kaseya’s virtual systems that affected 1500 businesses and carried a hefty ransom of $70million.
What Are People Doing to Stop It?
With cybercrime surging, leading organisations have taken a proactive approach to safeguarding their data assets. Some of their primary defensive activities have included the following:
Introspection & internal audits: The first point of departure when addressing vulnerabilities has come from acknowledging they exist in the first place. This is achieved by conducting extensive and thorough audits of the internal systems, technologies, and processes. Furthermore, the more often these reviews take place, the better prepared the organisation becomes to address evolving threats.
Increase monitoring: Setting up the systems is only half the job done. Top organisations have allocated a considerable amount of resources to the constant monitoring of cybersecurity structures. The scale and scope of the monitoring varies from organisation to organisation however the key factor lies in the recognising that it is a valuable component of the security posture to begin with.
Automation & Artificial Intelligence: To support the human activities being conducted, automating certain processes as well as harnessing the power of AI has been widely successful in the fight against cyberattacks. For instance, Darktrace’s AI technology has been used to monitor behavioural shifts in email communications and rapidly detect, then flag possible vendor email compromise scenarios.
Outsource services: Lastly, top enterprises have relieved themselves of the burden of solving it all alone. Through leveraging the rapid deployment and scalability of managed security services, enterprises have been able to outsource the functions they don’t have the expertise or capacity to manage internally. The decision has also empowered them to maximise on the benefits of having a best of breed team always on call for the unexpected.
What Should You Do to Protect Yourself?
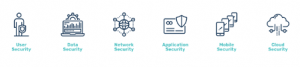
Map out your security surface: Knowing what to protect is just as important as understanding what to protect. DataGroupIT developed the 6 Pillar Model that ensures an organisation can rest assured that it has an end to end security solution in place. The model’s key areas are user security, data security, network security, application security, mobile security and cloud security.
Speak to the experts: Any plan of action needs to be carefully plotted. The best way to approach this is by combining internal discussions with external consultation. Service providers such as CyberSoc are well equipped to offer the necessary consulting services your organisation may need to enhance its cybersecurity plan. After all, spectators always see more than the players.
Develop a continuity plan: Planning for the worst possible outcome is the best possible way to ensure you’re never caught flat-footed. Envisioning how potential attacks may occur then drafting the corresponding continuity plans not only provides you with a measure of comfort, it ensures that the team is well prepared should a dreaded attack ever occur.
In conclusion, an ever-evolving cyber landscape will always be a cause for concern for organisations of all sizes, however understanding the nature of the threats then putting in the prerequisite steps in place to protect your enterprise is one of the best ways to safeguard your most valuable assets.
About DataGroutIT
DataGroupIT is Africa’s leading Value-Added Distributor (VAD). By partnering with the best selection of established and emerging technology vendors across the globe, we, provide complex solutions for any size business, including Enterprise and SME markets across the African continent.
Our product portfolio offers comprehensive solutions for IT Security, Infrastructure and Enterprise Software.
We are fully committed to our business partners. Channels & vendors success is our #1 mission. Our professional teams across Africa deliver exceptional sales, presale, logistic, marketing and financial support that create the ultimate platform to accelerate our business partners’ success.




