A cyber-criminal had already made the first steps of a critical intrusion at a European energy organization when the company deployed AI for cyber defense. Despite the attacker already lurking in the system, Darktrace was able to recognize that their activity deviated from the learned ‘pattern of life’ of the rest of the organization.
The hacker had compromised a desktop and established Command & Control (C2), downloading executable files disguised as harmless PNG files. But Darktrace autonomously grouped the desktop into a ‘peer group’ of similar devices, recognizing that it’s behavior was anomalous in comparison to the wider group.
The intrusion used many common evasion techniques to bypass traditional tools, including ‘Living off the Land’ techniques and masquerading malware behind commonly used file types. Upon Darktrace’s detection, later analysis of these ‘harmless’ files suggests they could lead to possible remote access of the compromised device, with use of the Metasploit framework.
Attack details
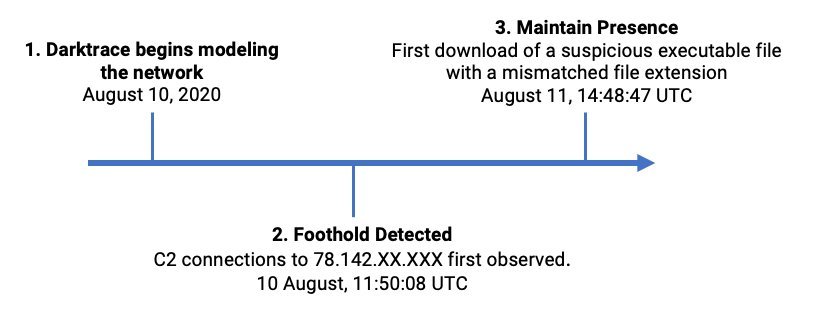
Figure 1: A timeline of the attack
Immediately upon installation, Darktrace began monitoring the behavior of around 5,000 devices, establishing their ‘pattern of life’, as well as that of their peer groups, and the wider organization. Just two hours into this learning process, an adminstator’s desktop was observed making suspicious connections to multiple domains hosted on IP 78.142.XX.XXX. The regular nature of these connections suggests that the infection was already established on the device.
The next day, the desktop was observed downloading a suspicious executable file named d.png, and multiple similar downloads subsequently occurred.
Executable files are often masqueraded as other file types in order to help bypass security measures, however the mismatched file extension here was immediately detected by Darktrace and flagged for further investigation.
A lack of OSINT for the download source at the time of this activity meant other security measures may have missed the suspicious HTTP connections. However, the rarity of the IP on the network alongside the unusual behavior in comparison to other network devices led Darktrace to quickly detect this malicious beaconing.
An overview of the infected device
After the first model breach, Darktrace continued to monitor the infected device, graphically representing the regular connections to the malicious endpoint w.gemlab[.]top. The device made several connections to this endpoint at precise, 3-hour intervals, suggesting some automated activity. No other devices in the peer group displayed this sort of behavior.
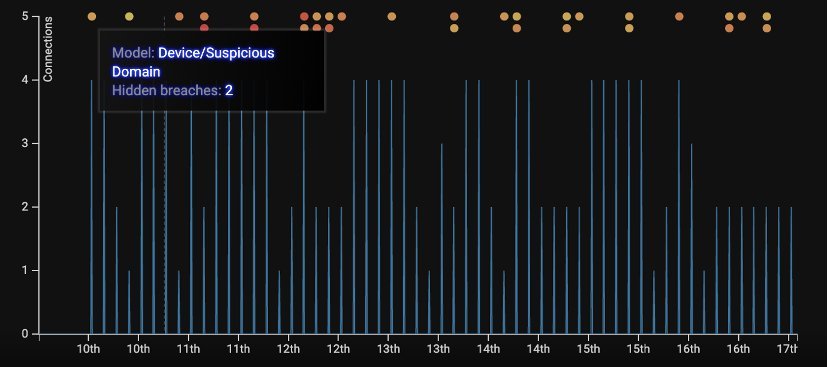
Figure 2: Darktrace presenting the connections in a graph, with model breaches represented by orange dots
Darktrace detected the suspicious nature of these HTTP connections, clearly surfacing the model breach for the security team to review and remediate.
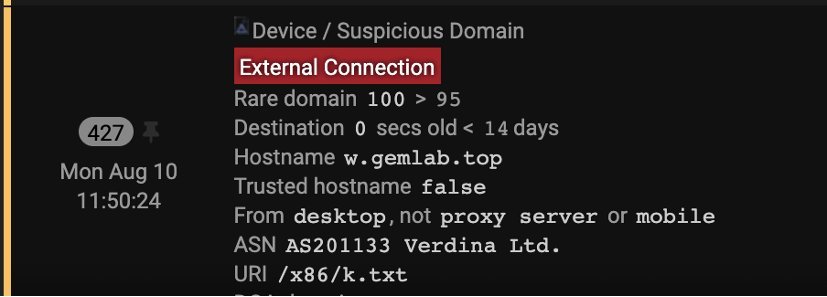
Figure 3: Darktrace surfacing high-level details of the model breach
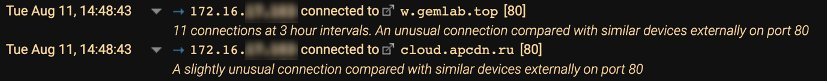
Figure 4: The device event log
Detecting a threat already inside
This example of a sophisticated attack shows an attempt to ‘blend in’ to the noise of regular traffic. However, Darktrace’s Immune System was still able to identify the signs of malintent, given its ability to auto-detect and cluster ‘peer groups’ of users and devices, thereby still recognizing abnormal behavior on the single compromised device. Despite only being active for a few hours, Darktrace immediately flagged the activity for further investigation.
Without Darktrace’s real-time detections and alerts – and a quick response from the security team to contain the threat — the potential ramifications of this intrusion can’t be understated. With effective command and control and sufficient privileges granted, cyber-criminals have been known to disrupt entire energy grids leading to mass blackouts in Ukraine and Estonia. Alternatively, hackers could have held large volumes of sensitive files to ransom, causing huge financial and reputational damage to the firm in question.
This isn’t the first time Darktrace has identified existing infections in customer environments – and it’s unlikely to be the last. A self-learning approach to cyber defence is not limited to identifying changes in the environment, but can detect existing compromises as well as novel and advanced attacks that evade traditional rules and signatures.
Thanks to Darktrace analyst Emma Foulger for her insights on the above threat find.
Original article from: Darktrace