The age old saying ‘teamwork makes the dream work’ is widely applicable in a multitude of environments and situations. Often applied to the sporting world, it’s just at home in the corporate setting. And there’s no place where it rings truer more than when it comes to structuring a cyber and info security team for your organisation.
Whilst most enterprises have a competent cybersecurity team, the efficacy of the team is often limited by the lack of key resources that complete the group holistically.
In its 2021 IT Roadmap for Cybersecurity, Gartner expanded on the key roles required to develop a robust cybersecurity approach posture. In this blog we’ll unpack those findings and lay out the primary takeaways you can adopt in the journey towards putting together an agile and future-facing collective of IT professionals for your organisation.
According to Gartner, the recommended functions and their roles to ensure the highest probability of cybersecurity success are as follows:
CISO: Responsible for the development of the cybersecurity strategy and program. The CISO ensures the cybersecurity strategy is aligned with the business strategy and objectives. They should also be responsible for directing assessments, mapping the action plan and executing it, as well as communicating the strategy’s progress across the organisation and with key stakeholders.
CIO: Works with the organisational leaders and guides the building of the cybersecurity program as well as communicates the strategy and objectives across the organisation.
Technical Team: Design, implement or improve, and maintain the organisation’s security architectures, policies and procedures. Furthermore they monitor and evaluate cybersecurity performance and improve it on the basis of new threats. Constant skills development is a must for this team.
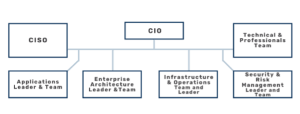
Application Leader & Team: Key partner for the CISO who should be tasked with assisting with the implementation and operation of key elements of security programs and operations.
Enterprise Architecture Leader and Team: Collaborate with the CISO and other IT leaders to make sure that security strategy and architecture are aligned and incorporated into overall enterprise architecture.
Infrastructure and Operations team and leader: Key partner for the CISO that assist with implementation and operation of key elements of security program and operations.
Security and Risk Management leader and team: Partner with the CISO to incorporate cybersecurity into overall governance, risk and compliance program and processes.
The above cybersecurity team structure is what is commonly adopted by the most successful companies that have been able to establish cross-functional teams for the cybersecurity initiatives.
It is no secret though that the acquisition, development and synergising of a team can be a challenging process. While critical for organisations, the gradual process can be supported by leveraging service providers that can shoulder the heavy lifting while your organisation focuses on capacitation.
This is why Africa’s largest companies harness the power and scalability of managed cybersecurity firms such as Cybersoc.
Regardless of where your organisation is in its cybersecurity journey, adopting the industry’s best practice measures is one of the best ways to guarantee ensuring a sturdy security posture.
To find out more about how DataGroupIT and our network of vendors can assist you in implementing best of breed cybersecurity solutions, kindly contact us on info@datagroupit.com or view our full suite of services here.




