The future of technology is limitless. Technological advances have been accelerated through increased network agility, integrated artificial intelligence (AI) and the ever-evolving Internet of Things. All of this has culminated in building the capacity to deploy, automate and orchestrate diverse use cases at hyperscale. As exciting and revolutionary as this fast-paced technological progression is, it also presents completely new security challenges.
For instance, the Internet of Things, or “IoT”, is made up of devices that connect to the internet and share data with each other. IoT devices include not only computers, laptops and smartphones, but also objects that have been equipped with chips to gather and communicate data over a network. By 2025, it is estimated that there will be more than 30 billion IoT devices. IoT is clearly a big deal. IoT has the potential of being the protagonist in tomorrow’s tale of technological revolution, but every protagonist must face an antagonist.
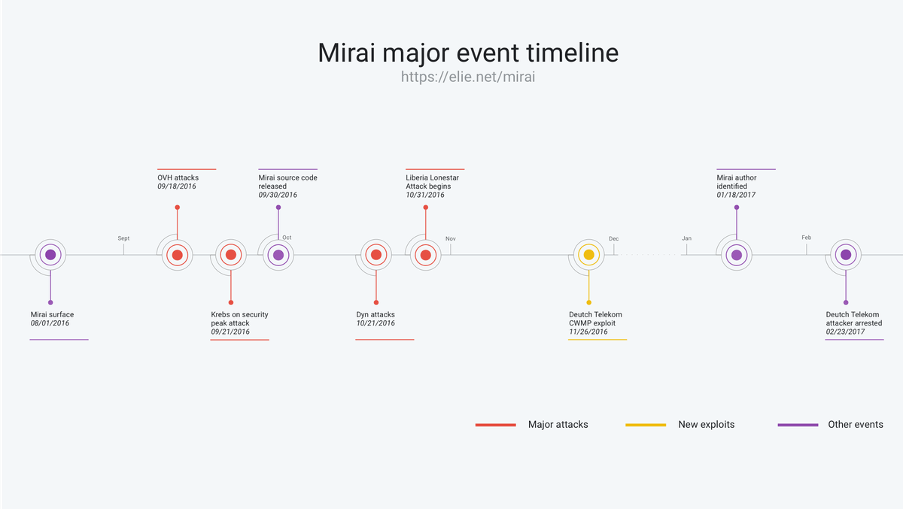
New technologies always have the potential of increasing the cyber-attack surface area and IoT is no exception. In 2016, the Mirai malware took full advantage of this. It has been responsible for some of the largest Distributed Denial Of Service (DDOS) attacks in the world including one on French cloud computing company, OVH. Attacks were carried out via IoT devices such as home routers, air-quality monitors, and personal surveillance cameras. Mirai went on to infect over 600,000 vulnerable IoT devices from August 2016 to February 2017 according to the below event timeline by Cloudlfare.
IoT security is a point of departure for this article but new technologies generally face threats because of similar reasons such as vulnerabilities that are yet to be discovered in the new technology. Zero-Trust Architecture immediately comes to mind. Traditional security models operate on the outdated assumption that everything inside an organisation’s network should be trusted. The Zero Trust model recognises that this trust is a vulnerability and that once on the network, users are free to access your data. The point of infiltration of an attack is often not the target location, knowing this and securing your network from it becomes even more critical in the case of multiple IoT devices.
New and exciting IoT applications will continue to emerge but so will new cyber-security risks. In the realm of new technologies, only a Zero-Trust model supported by real-time, self-learning cyber-security tools to defend against zero day attacks will suffice. Possessing legitimate insights into the realities and potential risks of new technologies is a non-negotiable. Palo Alto Networks not only has the latest insights on the continually evolving cybersecurity landscape, but also has the actionable steps required to Secure IoT Devices in the Enterprise.
Palo Alto Networks comprehensive IoT Security Solution stands out in the cybersecurity industry as a result of their ability to stay ahead of the curb. This was demonstrated in several webinars Palo Alto Networks conducted in collaboration with DataGroupIT that provided valuable insights into their strong preventive strategy for reducing risk you can’t and automating responses while gaining intelligence with each incident.
About DataGroutIT
DataGroupIT is Africa’s leading Value-Added Distributor (VAD). By partnering with the best selection of established and emerging technology vendors across the globe, we, provide complex solutions for any size business, including Enterprise and SME markets across the African continent.
Our product portfolio offers comprehensive solutions for IT Security, Infrastructure and Enterprise Software.
We are fully committed to our business partners. Channels & vendors success is our #1 mission. Our professional teams across Africa deliver exceptional sales, presale, logistic, marketing and financial support that create the ultimate platform to accelerate our business partners’ success.
Contact Us today to find out more.




